Google BeyondCorp Enterprise is a zero-trust and subscription-based security solution provided by Google. It is designed to provide easy and secure on-premise and cloud-based access to valuable corporate applications. Yes, riding on the zero-trust bandwagon is hardly a surprise for Google, considering its pioneering work on this model back in the early 2000s.
Once perfected, Google made BeyondCorp Enterprise widely available back in early 2021 and has continued to add new features all along. Whatever the modifications came over time, the core approach has stayed the same: Beyond Corp adds an agentless overlay to your existing security infrastructure, secures access for individual users and applications based on the context, and minimizes legacy access control approaches.
Sounds good so far? Let’s see how it works in practice.
Google BeyondCorp security features
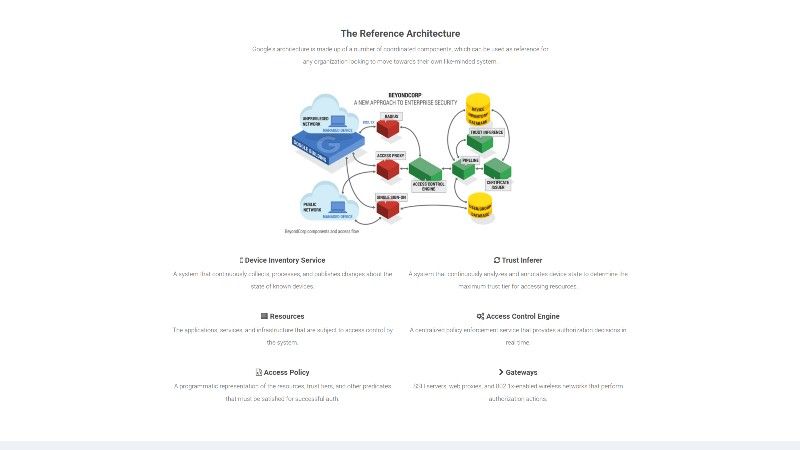
The BeyondCorp was designed in response to Operation Aurora, a high-profile APT attack that took place back in 2009. This led Google to reconsider its security model and move it beyond the concept of an almighty perimeter. Instead of it, Google BeyondCorp moves all applications to the public internet and makes them accessible through two main approaches: authorization workflows and authentication at the level of a single device.
At the heart of this model is the Zero Trust concept in which nothing is assumed when verifying one’s identity. This means that whenever an employee tries to connect to protected services or assets BeyondCorp will not use the network from which the access request has been made as a reference point for security verification. Instead, it will rely on the specific context relevant to that user and their device. The final outcome should be comprehensive insulation from the cybersecurity risks such as data leakage, malware and phishing attacks, theft of corporate information, etc.
The solution supports certificate-based access via VPC Service Controls which protects the users against credential thefts and accidental exposure. This is made possible by granting access only after being presented with both the device certificate and user credentials.
Next, you have the On-premises Connector which is tasked with forwarding Google Cloud-based Identity-Aware Proxy traffic to virtual machines and applications in environments beyond the Google Cloud.
Threat and Data Protection Services feature an array of services that gather security intelligence and help your system steel itself against data leakage, malware contamination, and access to malicious sites.
Also, the Endpoint Verification feature allows administrators to create a list of devices and define security posture for each of them.
Custom zero-trust access policies are easily definable and deployable with the help of the Access Context Manager. You can limit the access by the time and date and the strength of a particular credential.
Other supported security features include application-based segmentation, one-time passwords, SMS codes, 2SV keys, push notifications, pre- and post-login risk assessments, built-in public SSL certificate management, global load balancing, and DDoS protection.
BeyondCorp is seamlessly integrated with Google’s popular Chrome browser which allows it to market BeyondCorp as an agentless and proxy-less solution many users should be familiar with from the outset.
Management features
Manager features of the BeyondCorp solution are designed around the notion of easy accessibility and user familiarity, and it does show here.
First of all, you get to manage user profiles with the help of the Chrome browser. This means that no matter if you have your workforce bring their own devices (BYOD) or share corporate ones, all security features will be available at any time and any place.
Access policies can be managed and controlled via the administration console whenever the users sign into the Chrome browser from any platform. The management of their accounts can be done via Chrome Enterprise, Google Workspace, or Cloud Identity.
Administrators also get the opportunity to make use of the Endpoint Verification feature to get valuable information on the devices from which access to corporate assets is being sought. You can use this data to inform the fine-tuning of the access policies you want to enforce, including the option relating to password management, safe browsing and extension management, and others.
Apart from policies, you can also enforce BeyondCorp Enterprise threat and data controls at the profile level. Based on this, you can protect the users from malware-ridden sites and check the access requests for sensitive data, as well as submit suspicious files for analysis.
Another valuable option includes security event reporting for managed user profiles. These are used to get insights into the activities of high-risk users, data protection, and threat reports.
Google BeyondCorp interface
Finding your way around with Google BeyondCorp should be easy, at least if you are familiar with any of Google’s products, such as the Chrome browser.
Upon signing in to a new profile, accessing protected profiles via Chrome is as intuitive as it gets. In line with predefined access policies, end users may be asked to submit additional information when signing on, including two-factor authentication. What follows involves just taking note of provided instructions for the completion of the Google sign-in process.
After this, users will be presented with a message that they are now part of a Managed Chrome Profile which is subject to the enforcement of security policies by the administrator. Once the Chrome Sync kicks in, the implementation of the corporate security policy is finished and the users can proceed with their standard tasks.
The familiarity with Google’s ubiquitous products is certainly a plus here since the majority of users will have an easy time navigating its rather familiar interface.
Pricing
You can avail yourself of BeyondCorp Enterprise features at $6 (U.S. dollars) per user per month. Once paid, you can secure access to all web applications hosted on Google Cloud, third-party cloud services platforms, and on-premises, as well as power up your Google Chrome to handle incoming threats.
Just bear in mind that some of these features need to be paid for, as opposed to those described as “baseline” which are already featured as part of the Google Cloud package.
For example, restricting access to the Google Cloud Console and APIs based on IP or location is a feature supported with both paid and baseline options. On the other hand, device-based rules are only available as a paid option.
The easiest way to decide if six dollars is too much for what is being offered here is to check the list of both paid and baseline features here.
Final verdict
If you are after a zero-trust model implementation by a veteran provider, Google BeyondCorp Enterprise is a fast, accessible, and affordable option to minimize security incidents, prevent malicious attacks and reduce your exposure.
Google has another thing working for it and that is the familiarity of its brand and the Chrome browser which is seamlessly integrated with the BeyondCorp Enterprise. The price of admission is fair, so Google fans will need no convincing here, while the other user will find much to like here if they want at least a preview of what the zero-trust approach can do for their security.